
Cross-site request forgery (CSRF) is a type of security vulnerability that allows an attacker to trick a user into performing an action on a website that they did not intend to do. This can be used to transfer money, steal data, or even take control of a user’s account.
CSRF vulnerabilities are often found in web applications that use forms to submit data to the server. When a user submits a form, the browser sends the form data to the server along with a hidden field called the “CSRF token”. The CSRF token is a unique value that is generated for each form on the website. The server uses the CSRF token to verify that the request is coming from a legitimate user.
An attacker can exploit a CSRF vulnerability by tricking a user into visiting a malicious website that contains a form that submits data to the vulnerable website. The form will include the CSRF token from the vulnerable website, so when the user submits the form, the attacker will be able to perform the action that the form was designed to do.
For example, if a website allows users to transfer money between their accounts, an attacker could create a malicious website that contains a form that submits a transfer request to the vulnerable website. The form would include the CSRF token from the vulnerable website, so when the user visits the malicious website and submits the form, the attacker will be able to transfer money from the user’s account to their own account.
CSRF vulnerabilities are a serious security risk, and they should be taken seriously by website owners and bug bounty hunters. In this blog post, we will provide an in-depth guide to CSRF, including how to find and exploit CSRF vulnerabilities.
How to Find CSRF Vulnerabilities
There are a few different ways to find CSRF vulnerabilities. One way is to use a tool like OWASP ZAP or Burp Suite to scan a website for CSRF vulnerabilities. These tools can automatically identify forms that may be vulnerable to CSRF, and they can also help you to generate CSRF payloads that can be used to exploit the vulnerability.
Another way to find CSRF vulnerabilities is to manually test a website. To do this, you would need to identify all of the forms on the website that submit data to the server. Once you have identified the forms, you would need to try to submit them using a malicious website that contains the CSRF token. If the form is submitted successfully, then the website is likely vulnerable to CSRF.
How to Exploit CSRF Vulnerabilities
In this section, we will discuss the steps to exploit a CSRF vulnerability using an example. Let’s assume that we have identified a CSRF vulnerability in an online shopping application that allows users to add items to their cart. The goal is to exploit the vulnerability to add an item to the victim’s shopping cart without their knowledge or consent.
Step 1: Analyze the Request
First, analyze the request made by the web application when a user adds an item to their cart. This can be done using a web proxy like Burp Suite or a browser’s developer tools. Look for any unique parameters, such as the user ID, item ID, and the quantity of the item being added.
Example Request:
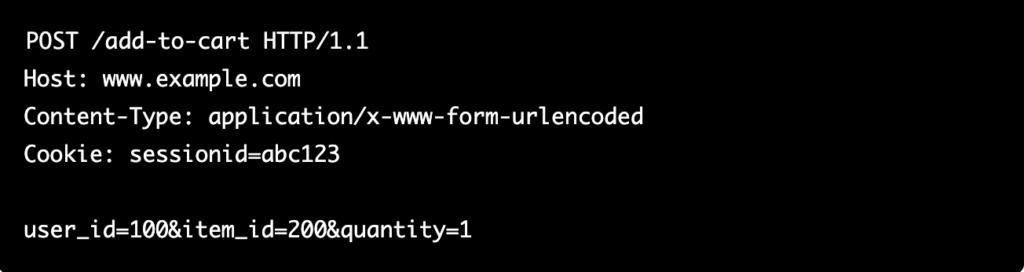
Step 2: Craft the CSRF Payload
Create an HTML form that replicates the request made by the application when adding an item to the cart. The form should include the necessary input fields and be set to automatically submit upon loading. For this example, we’ll create a form that adds item 200 to the victim’s cart.
Step 2: Craft the CSRF Payload
Create an HTML form that replicates the request made by the application when adding an item to the cart. The form should include the necessary input fields and be set to automatically submit upon loading. For this example, we’ll create a form that adds item 200 to the victim’s cart.
Example CSRF Payload:
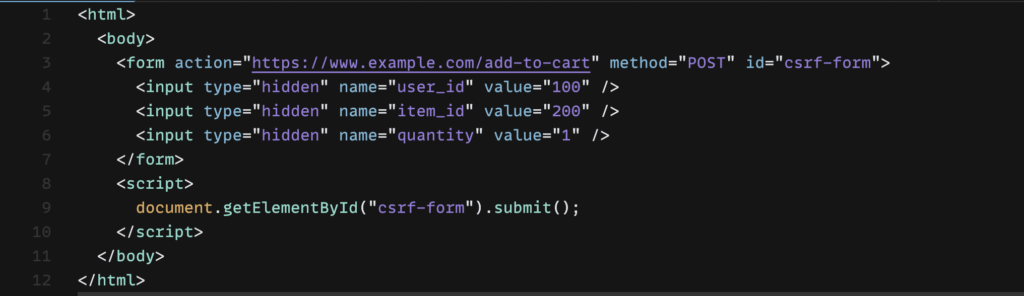
Step 3: Deliver the CSRF Payload
Next, you need to deliver the CSRF payload to the victim. This can be achieved using social engineering tactics, such as sending an email containing a link to the malicious website or embedding the payload in a website the victim is likely to visit. Once the victim clicks on the link or visits the website with the embedded payload, their browser will automatically submit the form, triggering the CSRF attack.
Step 4: Verify the Exploit
To confirm the success of the exploit, check whether the item was added to the victim’s cart. This can be done by monitoring the victim’s account on the shopping application or by asking the victim to confirm if the item was added. Successful exploitation indicates that the CSRF vulnerability can be used to perform actions on behalf of the victim without their consent.
How to Protect Against CSRF Vulnerabilities
There are a few different ways to protect against CSRF vulnerabilities. One way is to use a CSRF token. A CSRF token is a unique value that is generated for each form on the website. The CSRF token is included in the form data that is submitted to the server, and the server uses the CSRF token to verify that the request is coming from a legitimate user.
Another way to protect against CSRF vulnerabilities is to use a double submit cookie. A double submit cookie is a technique that uses two cookies to protect against CSRF vulnerabilities. The first cookie is the CSRF token, and the second cookie is a session ID. The server uses the CSRF token to verify that the request is coming from a legitimate user, and the server uses the session ID to track the user’s session.
Conclusion
CSRF is a serious security risk, and it should be taken seriously by website owners and bug bounty hunters. In this blog post, we have provided an in-depth guide to CSRF, including how to find and exploit CSRF vulnerabilities. We have also provided some tips on how to protect against CSRF vulnerabilities. We hope that this blog post has been helpful, and we encourage you to learn more about CSRF and how to protect against it.

