Think about a scenario in which your organization was the victim of a big data breach that required you to shut down your network for a few hours. If you believe the attackers have been unplugged from your network, you alter the firewall rules and configure your intrusion detection and prevention systems to prevent the attackers from re-entering your network. Is this true, though? Is it true that they’ve vanished? Or is it only a matter of time before you discover the exact opposite of what you believe?
Once the attacker has gained access to your network, he will take steps to guarantee that the network’s persistence is maintained. This will ensure that even if he becomes disconnected (for a variety of reasons), the victim host will automatically rejoin to him. This is one of the steps in the post-exploitation process that an attacker will carry out. A variety of methods can be used to accomplish this.
Some of them are:
- Dumping the password hashes in the hopes of gaining access to the system’s credentials, which can then be used to gain access to other systems afterwards.
- Searching for credentials that have been stored on other systems and that can be used to gain access to those other systems.
- Chaining the registry (for Windows OS)
- Scheduling tasks that make a connection to the attacker machine like we have cron-jobs in the Linux
- Installing a malicious app that starts every time at the startup and initiates a connection to the attacker’s machine mostly by using backconnect shell.
After reviewing all of the ways listed above, a user with some technical skill can readily determine that something is wrong, and the points listed above are among the first things that he will search for in order to determine what the problem is. So, what exactly is left for the assailant now? He cannot execute code on the machine or sustain persistence if the majority of the factors listed above are unreliable, which is the case.
In this case, the answer is DLL Hijacking. In this blog post, we’ll go over what DLLs are and what DLL hijacking is, as well as see a practical demonstration of both.
What is a DLL?
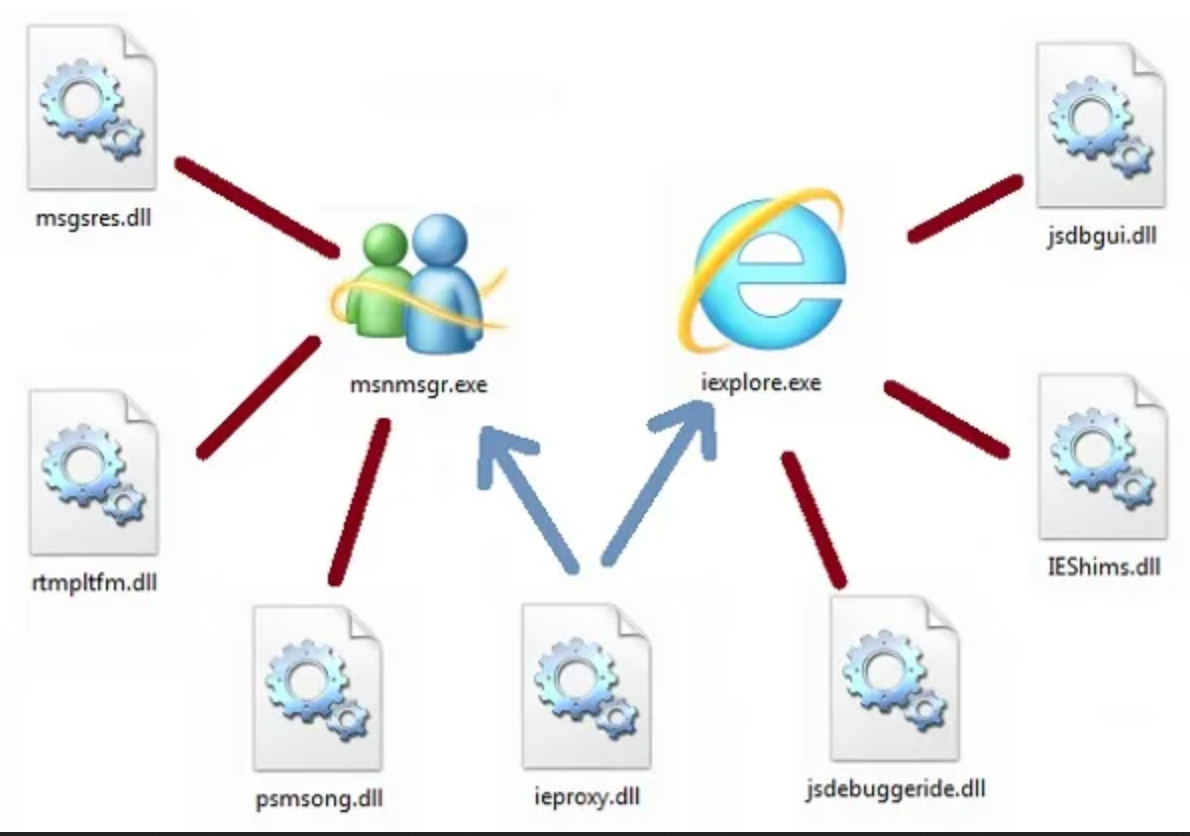
DLL is an abbreviation for Dynamic Link Library. They contain the.dll extension and behave similarly to an executable, except that they are not directly executable. But what is the point of having them?
They are public libraries that are open to the public. It is not uncommon for two or more applications to be required to do the same task. For example, you could display a pop-up box. In practice, it is not possible to write the same piece of code in multiple programs/software/executable in order to achieve the same result as one would expect. As a result, you can import a DLL that will perform this function for you. This would save you from having to write a few lines of code, and your code would appear more modular and less buggy as a result.
What is PATH?
The question is, how does the executable code know where to find the DLL that it needs to load? Let’s have a look and see. The PATH variable is an environment variable that is used to direct the user to a certain location. Any Operating System uses the PATH variable to determine where to look for a command when it is executed. If the command is not found in the current working directory, the PATH variable instructs the OS where to look. Actually, it operates in the same way as your home address and phone number do: if your home address is not located in the first instance, your phone number will be utilized to determine the correct address of your residence.
To print the PATH variable in Windows
echo %PATH
In Linux/MacOS
echo PATH
Understanding the normal flow of execution.
For the sake of this example, let’s say that we have a file called listfiles.exe in the Desktop directory. This executable depends upon list.dll. But the list.dll does not exist in the Desktop directory. So, what your Operating System will do in the background is, it’ll check the contents of the PATH variable and check for the existence of the list.dll in each of the directories listed in the PATH variable if the file is found, it will be executed other error will be shown.
Demonstration:
Let’s try to build on what we’ve learnt and try to create an executable file that executes a DLL.
For the sake of this demonstration, we’ve got 2 files written in the C language. The first executable checks the presence of a malicious.dll file as evident from the code provided below.
#include <windows.h>
#include <stdio.h>
int main(void)
{
HINSTANCE dll;
//LoadLibrary helps to load a librarby
dll = LoadLibrary(TEXT("malicious.dll"));
if(dll != NULL)
{
printf("DLL Found & Executing");
}
else
{
printf("Error");
}
return 0;
}We’ve imported the standard stdio.h and windows.h library. Windows.h is used to access the built-in Windows API functions.
As per Microsoft’s documentation:
hInstance is something called a “handle to an instance” or “handle to a module.” The operating system uses this value to identify the executable (EXE) when it is loaded in memory.
The LoadLibrary() functionis used to load the malicious.dll DLL. If found, it’ll print “DLL Found & Executing”, otherwise it’ll print “Error”
The second file is a dll file.
#include <windows.h>
BOOL WINAPI DllMain (HANDLE dll,DWORD dwReason, LPVOID ldReserved)
{
switch(dwReason)
{
case DLL_PROCESS_ATTACH:
MessageBox(NULL, "DLL Hijakced", "Hacked", MB_ICONERROR | MB_OK);
break;
}
return TRUE;
}We’ve used a MessageBox function. As per Microsoft documentation, the MessageBox function, “displays a modal dialog box that contains a system icon, a set of buttons, and a brief application-specific message, such as status or error”.
In our Case, it’ll print “DLL Hijacked” as a part of the body with a title of “hacked”. When this dll is executed, a dialog message box will appear with an error icon and with an OK Button.
The error icon will be because of MB_ICONERROR parameter and an OK Button will appear because of the MB_OK parameter that we’ve supplied as shown below.
Now that we’ve got both the files ready, let’s compile them.
We’ll be using a cross compiler called x64_64-w64-mingw32-gcc-win32. A cross compiler generates executable files for OS other than the host OS in which it is running. In our example, we’ll be using it to generate executable files for Windows machines.
To install x86_64-w64-mingw32-gcc-win32 on Linux distributions, you can use the following command.
sudo apt-get install gcc-mingw-w64
OR
yum install acc-mingw-w64
The former is to be used in case your package-manager is apt-get and the latter if your package manager is yum.
To generate files,
x64_64-w64-mingw32-gcc-win32 loaddll.c -o loaddll.exex64_64-w64-mingw32-gcc-win32 malicious.c -o malicious.dll -shared
Now, all you have to do is transfer these files to the Windows host machine. You can experiment around a bit. For example, just transfer the loaddll.exe file to the windows host and then try executing it. It’ll return Error. This is because we’ve not copied the malicious.dll file to the host computer. Now copy the malicious.dll file to the Windows host and try executing the loaddll.exe file. You’ll find that a message box appears on the screen with the message “DLL Hijacked”.

Note: You might need to turn off Windows Defender for this to work. There are techniques to evade Windows Defender, but that would have further made this blog-post more complex.
We’ve created our own malicious dll and executed it with a program that we just wrote. An attacker would create a malicious dll that would execute some code on the victim host. This is how an attacker can execute code on the victim machine without being caught for a very long time, because no would spin up the process monitor and check which dll is each process running.
Conclusion
In DLL Hijacking, an attacker can use your computer’s DLL files to execute unexpected code on it. This means that if an attacker is able to obtain a file on your computer (via social engineering, remote control, or other means), that file could be executed when a user starts an application that is vulnerable to DLL Hijacking (such as a web browser). Hence it is important that the file should have to be scanned or use of antivirus is encouraged before executing any type of program on the system.

