
Many firms were forced to close their doors and many others went out of business as a result of attackers hacking their networks and bringing their systems to a halt. With more organizations coming online every day, it has become increasingly more critical to assist them in securing their boundaries and assets before criminals take advantage of their vulnerabilities. Businesses are becoming more aware of the benefits that cybersecurity may provide and are signing up for the services.
Now this brings us to a question. What is cybersecurity?
Cybersecurity is the process or practice of protecting computer systems, network devices, and data from cyber-attacks. It is also referred to as computer security and information security.
The majority of people confuse cyber security with hacking and penetration testing, which are actually two different things. Cybersecurity is a large and diversified topic, and there are many more career options available in the cybersecurity business than you may think.
Some of them are:
- Chief Information Security Officer
- Security Analyst
- Incident Responder
- Penetration Tester
- Security Architect
- Security Specialist/Consultant
Before moving on to the technical stuff, it’s important that we talk about Vulnerabilities.
Often while developing applications, software, etc. developers make mistakes. These mistakes could be in the form of insecure coding practices, such as using harmful functions or methods, business logic issues, etc.
A vulnerability is a flaw in an application that can be exploited by an attacker to get access to sensitive information.
Vulnerability Assessment
Vulnerability Assessment refers to the process of identifying security vulnerabilities and risks in a target, but not exploiting them.
It’s also important to note that a vulnerability assessment can either be performed manually or using automated tools. But what’s the difference?
Each technique has its own set of benefits and drawbacks to consider. Although an automated tool or scanner can provide you with information rapidly, the number of false positives in the results generated will be higher. A manual approach can take a significant amount of time to complete, but it allows you to check for logic vulnerabilities that are generally outside the scope of an automated tool, which is advantageous.
Exploit
An exploit is a code instruction that can be used to take advantage of a vulnerability in a computer system or application. The vulnerability can be exploited with the help of the exploit code, such as compromise of data is only possible with the help of exploit. Nowadays, the majority of exploits may be found on the internet.
Whenever a software manufacturer becomes aware of a vulnerability in his application, he immediately issues an update (also known as updates) to patch this vulnerability so that the vulnerability can’t be exploited further.
0-day Vulnerabilities
When a vulnerability in an application or a device has recently surfaced and the software vendor (the manufacturer or the developer) is not aware of it or there are no patches available for that particular vulnerability, the vulnerability is referred to as a zero-day vulnerability (zero-hour vulnerability).
Since, the software vendor isn’t aware of it, it’ll take him a considerable amount of time to release the patch, depending upon his team and criticality of the vulnerability. As a result, these vulnerabilities are more critical since, if the updates are not deployed, organizations become less safe and there is a high likelihood that the vulnerability will be exploited within their systems.
Threat
Threat is any intent of malicious attack that seeks to cause harm to your data, unlawfully access, destroy or tamper it.
Some of the common Cyber Threats are:
- Social Hacking
- Ransomware
- Unpatched Vulnerabilities.
Threat is simply the intention that these flaws will be exploited in the system, and as a result, we must implement safeguards to protect against such vulnerabilities.
Social Hacking
Social Hacking is also known as Social Engineering. It is exploiting human weaknesses or manipulating people so that you can make them do certain things that they would normally not have done, like reveal personal information, One-time Passwords, etc. or clicking on a link that could lead to a phishing page or downloading and installing malware on the computer If the user goes through with his actions, a variety of things could go wrong, including the compromise of important data.
Ransomware
Ransomware is a type of malware that encrypts all your personal data. Once all your personal data is encrypted, the attackers can then demand for a ransom before they decrypt your data. They could copy all of the information from your computer and threaten you with leaking the information. However, the majority of the time, ransomware is propagated through malicious email attachments or the installation of questionable software.
Even if you pay the ransom in full, there is no guarantee that they will successfully decrypt your information. So, it is always advised to keep a backup of things of your data.
Risk
Risk can be defined as the potential harm that an attacker can do to your organization if they successfully exploit a vulnerability. It is possible to categorize risks according to their severity, such as loss of reputation, financial resources, personal data, availability of services, and so on. Organizations identify the risks before deploying their services.
Now let’s try to fit in the terms that we just learnt.
Attackers try to exploit a vulnerability in order to gain unauthorized access to your network, or application. The assumption that a vulnerability might be exploited to compromise your user data might be considered as a risk. A vulnerability left unpatched is a threat to your organization and can cause a considerable amount of loss of financial resources and data.
Penetration Test
Pen testing is the process by which an individual or a group of individuals collaborate to identify and exploit vulnerabilities in an application or a system in order to ensure that they are protected. This is done in order for them to gain access to an organization’s security posture and then inform them of their vulnerabilities. The organization will then be able to address such vulnerabilities, and as a result, the attackers will no longer be able to take use of them.
Scope
Whenever you perform a Penetration test or a Vulnerability Assessment, there is always a scope defined. A scope can be considered a boundary out of which you aren’t allowed to go. Suppose an organization tells you to perform a penetration test on their website, www.example.com. Then in this case, you can only perform a penetration test on the website. You aren’t allowed to access and test their network.
Protocols
Imagine that the only language that you know is English. Can you communicate with a person who speaks Russian? Probably not. This can be attributed as a communication gap or barrier. You can communicate with him if you know Russian or you can hire someone who can translate your words to the Russian language and vice-versa.
Similarly, devices connected to each other via the internet, can’t communicate with each other without a set of rules set into place. These rules are called protocols.
These rules govern the communication between 2 devices. They define the format depending upon the service that they are communicating on.
There are different protocols for web applications, voice calls, etc. Different types of communication have different types of rules such as the Mail Transfer protocol is different from the File Transfer protocol.
To get a grasp of the protocols, you can start off by learning about the OSI and the TCP/IP Model.
HTTPS
HTTP is a simple plain text protocol, which means that all the communication happens in plaintext. Any attacker, with access to proper tools can know what is being transferred. Something had to be done to prevent this.
The solution was to encrypt the data so that even if it is captured by the attacker, the attacker will not be able to make sense out of it.
So, HTTPS was born. HTTPS stands for HyperText Transfer Protocol Secure. What it does is, whenever you request for your favorite web page or other resources, the web server will first encrypt it and then send it to you. When it is received by your browser, it is first decrypted and then shown to you.
In this scenario, since the web page is encrypted, even if the attacker manages to get hold of the communication, he’ll not be able to decrypt it.
Ports
At any given point of time, there could be hundreds of programs and services running on a device communicating with each other or other devices over the internet.
In order for these services to communicate with each other, it is necessary to identify them uniquely as they are a part of the same device. It can be done with the help of port numbers. There are 65536 ports, from 0 to 65535 (including 0).
Each new service/program capable of communication over the network can be accessed by a port.
For example, your IP address is 10.10.10.1. You install MySQL on it. MySQL is a database that can be accessed via the port number 3306.
You can access the database by typing in mysql –u root –p –h 10.10.10.1:3306
Ignoring the other parameters, you can see that in order to access MySQL, you have to reach the port 3306 on the IP 10.10.10.1 (i.e., 10.10.10.1:3306)
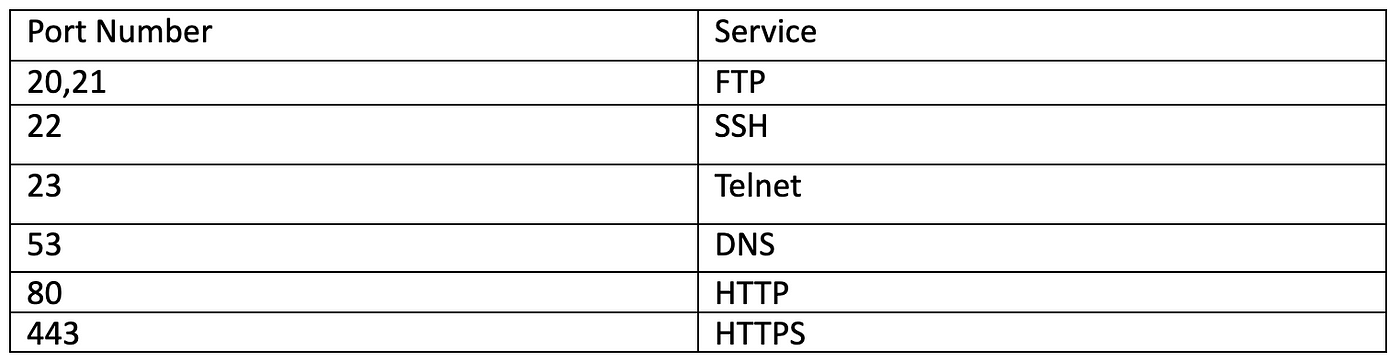
Some of the services, and their respective port numbers are
Further Learning
If you want to learn more about cyber security, and specifically about Web Application security, you can use the OWASP’s resources, such as the vulnerability categorization and cheatsheets, to assist you learn more about the subject. They include a wide range of vulnerability mitigations and best practices, which you may use to learn more about cyber security and become more knowledgeable.
Conclusion:
In this day and age, cyber attacks are becoming more common, and it is everyone’s obligation to protect the security of an organization. The number of criminals continues to outweigh the number of defenders. A robust cybersecurity posture can assist you in reducing the likelihood of cyber attacks. As a result, it is critical that you have a solid understanding of the fundamentals and fundamentals of security.





